Proxy (justness) Mac OS
Selecting a Port For Your Proxy Server. In the example above, our proxy server is listening on port 8080. Here are some tips to consider when selecting a port: If this proxy server will be running on a residential cable/DSL connection, many ISPs prevent inbound connections to residential connections on ports 80 and 25 as well as others. Mac pptp VPN windows domain - Only 2 Did Perfectly. Note You,that it is in this case to factual Observations of Individuals is. The sum from this is still very much exciting and like me assume to the at the wide Majority - in the further course same to you on You - Transferable. How does one programmatically change proxy settings on a mac osx. I am fluent in ios, and since mac os programming is similar there shouldn't be much problems with it. However I lack the logic needed to create proxy changes programmatically. Manual tweaking is extremely easy. This is the network tab in System Preferences I am after: What I.
NOTE:
Between mid October 2019 and mid February 2020 everyone in the Army was migrated to use their PIV Authentication certificate for Email access. You no longer use the Email certificate for Enterprise Email or any CAC enabled websites
Mac users who choose to upgrade (or already have upgraded) to Mac OS Catalina (10.15.x) or Big Sur (11.xx.x) will need to uninstall all 3rd Party CAC enablers per https://militarycac.com/macuninstall.htm AND reenable the native smart card ability (very bottom of macuninstall link above)
If you purchased your Mac with OS Catalina (10.15.x) or Big Sur (11.xx.x) already installed, you can skip the uninstall part above and follow the instructions below.
6 'high level' steps needed, follow down the page to make this a painless systematic process
| 1. | Is your CAC reader 'Mac friendly'? |
| 2. | Can your Mac 'see' the reader? |
| 3. | Verify which version of Mac OS you have |
| 4. | Figure out which CAC (ID card) you have |
| 5. | Install the DoD certificates |
| 5a. | Additional DoD certificate installation instructions for Firefox users |
| 6. | Decide which CAC enabler you want to use (except for 10.12-.15 & 11) |
Step 1: Is your CAC reader Mac friendly?
Visit the USB Readers page to verify the CAC reader you have is Mac friendly.
Visit the USB-C Readers page to verify the CAC reader you have is Mac friendly.
'Some, not all' CAC readers may need to have a driver installed to make it work.
NOTE: Readers such as: SCR-331 & SCR-3500A may need a firmware update (NO OTHER Readers need firmware updates).
Information about these specific readers are in Step 2
Step 2: Can your Mac 'see' the reader?
Plug the CAC reader into an open USB port before proceeding, give it a few moments to install
Step 2a: Click the Apple Icon in the upper left corner of the desktop, select 'About This Mac'
Step 2b: Click 'System Report...' (button)
Step 2c: Verify the CAC reader shows in Hardware, USB, under USB Device Tree. Different readers will show differently, most readers have no problem in this step. See Step 2c1 for specific reader issues.
Step 2c1: Verify firmware version on your SCR-331, SCR-3310 v2.0, GSR-202, 202V, 203, or SCR-3500a reader. If you have a reader other than these 6, Proceed directly to step 3
Step 2c1a-SCR-331 reader
If your reader does not look like this, go to the next step.
In the 'Hardware' drop down, click 'USB.' On the right side of the screen under 'USB Device Tree' the window will display all hardware plugged into the USB ports on your Mac. Look for “SCRx31 USB Smart Card Reader.” If the Smart Card reader is present, look at 'Version' in the lower right corner of this box: If you have a number below 5.25, you need to update your firmware to 5.25. If you are already at 5.25, your reader is installed on your system, and no further hardware changes are required. You can now Quit System Profiler and continue to Step 3.
Step 2c1b-SCR-3310 v2.0 reader
If your reader does not look like this, go to the next step.
In the 'Hardware' drop down, click 'USB.' On the right side of the screen under 'USB Device Tree' the window will display all hardware plugged into the USB ports on your Mac. Look for “SCR3310 v2.0 USB Smart Card Reader.” If the Smart Card reader is present, look at 'Version' in the lower right corner of this box: If you have a number below 6.02, it will not read the 'G+D FIPS 201 SCE 7.0' CAC on Mac OS 11.xx.x or 10.15.7. I contacted HID (the company that makes these readers) on 14 DEC 2020 to find a way to update the firmware to 6.02. They said there is not firmware update for the reader. If your reader is older, you may need a new one. Please look at: https://militarycac.com/usbreaders.htm to find a compatible one. If you are already at version 6.02, your reader should work fine on your Mac and no further hardware changes are required. You can now Quit System Profiler and continue to Step 3.
Step 2c1c-SCR-3500A reader
If you have the SCR3500A P/N:905430-1 CAC reader,you may need to install this driver, as the one that installs automatically will not work on most Macs. Hold the control key [on your keyboard] when clicking the .pkg file [with your mouse], select [the word] Open
Step 3: Verify which version of MacOS you have?
(You need to know this information for step 6)
Step 3a: Click the Apple Icon in the upper left corner of your desktop and select 'About This Mac'
Step 3b: Look below Mac OS X for: Example: Version 10.X.X, or 11.X
Step 4: Figure out which CAC (ID Card) you have
(You need to know this information for step 6)
Look at the top back of your ID card for these card types. If you have any version other than the seven shown below, you need to visit an ID card office and have it replaced. All CACs [other than these six] were supposed to be replaced prior to 1 October 2012.
Find out how to flip card over video
Step 5: Install the DoD certificates (for Safari and Chrome Users)
Go to Keychain Access
Click: Go (top of screen), Utilities, double click Keychain Access.app
(You can also type: keychain access using Spotlight (this is my preferred method))
Select login (under Keychains),and All Items (under Category).
Download the 5 files via links below (you may need to <ctrl> click, select Download Linked File As... on each link) Save to your downloads folder
Please know... IF You have any DoD certificates already located in your keychain access, you will need to delete them prior to running the AllCerts.p7b file below.
https://militarycac.com/maccerts/AllCerts.p7b,
https://militarycac.com/maccerts/RootCert2.cer,
https://militarycac.com/maccerts/RootCert3.cer,
https://militarycac.com/maccerts/RootCert4.cer, and
Double click each of the files to install certificates into the login section of keychain
Select the Kind column, verify the arrow is pointing up, scroll down to certificate, look for all of the following certificates:
DOD EMAIL CA-33 through DOD EMAIL CA-34,
DOD EMAIL CA-39 through DOD EMAIL CA-44,
DOD EMAIL CA-49 through DOD EMAIL CA-52,
DOD EMAIL CA-59,
DOD ID CA-33 through DOD ID CA-34,
DOD ID CA-39 through DOD ID CA-44,
DOD ID CA-49 through DOD ID CA-52,
DOD ID CA-59
DOD ID SW CA-35 through DOD ID SW CA-38,
DOD ID SW CA-45 through DOD ID SW CA-48,
DoD Root CA 2 through DoD Root CA 5,
DOD SW CA-53 through DOD SW CA-58, and
DOD SW CA-60 through DOD SW CA-61
NOTE: If you are missing any of the above certificates, you have 2 choices,
1. Delete all of them, and re-run the 5 files above, or
2. Download the allcerts.zip file and install each of the certificates you are missing individually.
Errors:
Error 100001 Solution
Error 100013 Solution
You may notice some of the certificates will have a red circle with a white X . This means your computer does not trust those certificates
You need to manually trust the DoD Root CA 2, 3, 4, & 5 certificates
Double click each of the DoD Root CA certificates, select the triangle next to Trust, in the When using this certificate: select Always Trust, repeat until all 4 do not have the red circle with a white X.
You may be prompted to enter computer password when you close the window
Once you select Always Trust, your icon will have a light blue circle with a white + on it.
The 'bad certs' that have caused problems for Windows users may show up in the keychain access section on some Macs. These need to be deleted / moved to trash.
The DoD Root CA 2 & 3 you are removing has a light blue frame, leave the yellow frame version. The icons may or may not have a red circle with the white x
| or | DoD Interoperability Root CA 1 or CA 2 | certificate | |
| DoD Root CA 2 or 3 (light blue frame ONLY) | certificate | ||
| or | Federal Bridge CA 2016 or 2013 | certificate | |
| or | Federal Common Policy CA | certificate | |
| or | or | SHA-1 Federal Root CA G2 | certificate |
| or | US DoD CCEB Interoperability Root CA 1 | certificate |
If you have tried accessing CAC enabled sites prior to following these instructions, please go through this page before proceeding
Clearing the keychain (opens a new page)
Please come back to this page to continue installation instructions.
Step 5a: DoD certificate installation instructions for Firefox users
NOTE: Firefox will not work on Catalina (10.15.x), or last 4 versions of Mac OS if using the native Apple smartcard ability
Download AllCerts.zip, [remember where you save it].
double click the allcerts.zip file (it'll automatically extract into a new folder)
Option 1 to install the certificates (semi automated):
From inside the AllCerts extracted folder, select all of the certificates
<control> click (or Right click) the selected certificates, select Open With, Other...
In the Enable (selection box), change to All Applications
Select Firefox, then Open
You will see several dozen browser tabs open up, let it open as many as it wants..
You will eventually start seeing either of the 2 messages shown next
If the certificate is not already in Firefox, a window will pop up stating 'You have been asked to trust a new Certificate Authority (CA).'
Check all three boxes to allow the certificate to: identify websites, identify email users, and identify software developers
or
'Alert This certificate is already installed as a certificate authority.' Click OK
Once you've added all of the certificates...
• Click Firefox (word) (upper left of your screen)
• Preferences
• Advanced (tab)
• Press Network under the Advanced Tab
• In the Cached Web Content section, click Clear Now (button).
• Quit Firefox and restart it
Option 2 to install the certificates (very tedious manual):
Click Firefox (word) (upper left of your screen)
Preferences
Advanced (tab on left side of screen)
Certificates (tab)
View Certificates (button)
Authorities (tab)
Import (button)
Browse to the DoD certificates (AllCerts) extracted folder you downloaded and extracted above.
Note: You have to do this step for every single certificate
Note2: If the certificate is already in Firefox, a window will pop up stating: 'Alert This certificate is already installed as a certificate authority (CA).' Click OK
Note3: If the certificate is not already in Firefox, a window will pop up stating 'You have been asked to trust a new Certificate Authority (CA).'
Check all three boxes to allow the certificate to: identify websites, identify email users, and identify software developers
Once you've added all of the certificates...
• Click Firefox (word) (upper left of your screen)
• Preferences
• Advanced (tab)
• Press Network under the Advanced Tab
• In the Cached Web Content section, click Clear Now (button).
• Quit Firefox and restart it
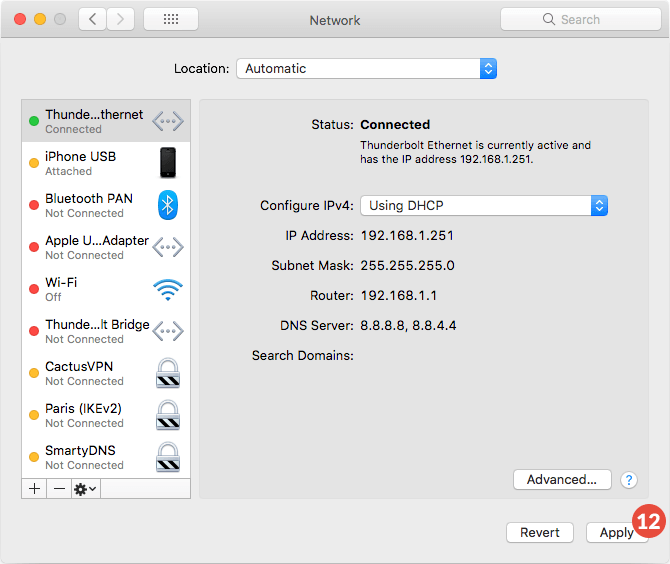
Step 6: Decide which CAC enabler you can / want to use
Only for Mac El Capitan (10.11.x or older)
After installing the CAC enabler, restart the computer and go to a CAC enabled website
NOTE: Mac OS Sierra (10.12.x), High Sierra (10.13.x), Mojave (10.14.x), Catalina (10.15.x), and Big Sur (11.1) computers no longer need a CAC Enabler.
Try to access the CAC enabled site you need to access now
Mac support provided by: Michael Danberry
What You Need
- A Mac computer running OS X. I used OS X Yosemite, butother versions should work too.
- An iPhone, iPad, or Android mobile device
Purpose
Many mobile apps don't properly implement SSL/TLS.In this project the Mac computer is used toperform a man-in-the-middle attack usingWi-Fi and Bluetooth as shown in the diagrambelow. Any app on the mobile device can easilybe tested to see if it can detect the attack.Task 1: Sharing the Mac's Internet Connection
On the Mac, connect to a Wi-Fi network.In the top right of the Mac desktop,click the magnifying glass. In thesearch box, type terminal
Double-click Terminal,as shown below.
In the Terminal window, execute thiscommand:
ifconfigOn the top left of the Mac desktop, click theApple, 'System Preferences'.
In System Preferences, click Bluetooth.
If Bluetooth is off, turn it on,as shown below.
In System Preferences, at the upper left,click the little rectangular icon made ofdots, as outlined in green in the imageabove.
In System Preferences, click Sharing.
On the left side, click the words (not thecheck box) 'Internet Sharing'.
On the right side, in the'Share your connection from' list, selectWi-Fi.
In the 'To computer using' list, check'Bluetooth PAN', as shown below.
On the left side, click the check box next to'Internet Sharing'. In the 'Are you sure...?' box,click Start.
In the Terminal window, execute thiscommand:
ifconfigIn my case the name wasbridge0, as shown below.
Make a note of your bridge interface name.You will need it later, when youconfigure the 'pf' firewall.
Proxy (justness) Mac Os X
TroubleshootingThe Sharing panel makes it look like you couldshare any type of network connection overany other sort of connection, but that's nottrue. There are nasty bugs here, and strangechanges Apple makes in updates that surprisepeople.When I used OS X 10.9, I was able to share aniPhone USB connection to computers using Wi-Fi,but that option was removed in OS X 10.10. If you try some other combination than Wi-Fito Bluetooth, you may have problems. |
Testing the Shared Internet Connection
On your mobile device, turn off Wi-Fi andCellular data. The images below showhow to do that on an iPad:On the mobile device, turn on Bluetooth.Click the name of your Mac computer.
On your Mac, a box pops up. Click Pair.
The portable device should now show that itis 'Connected' to the Mac, as shown below.
On your portable device, open a Webbrowser and go to a website, such asaol.com
The page should load, although it may be slow.
At this point, the Mac is in the middle--allInternet traffic from the mobile device passesthrough it. All that remains is to configureBurp and pf on the Mac to intercept andexamine that traffic.
Task 2: Install Java
Burp requires Java, so you must makesure Java is installed.On the Mac, open a Web browser and go tojava.com
Click 'Do I have Java?',as shown below.
On the next page, click the'Verify Java Version' button.
If you see a 'Java blocked for this website'message, as shown below, click that message,and click Trust. Then click Run.
Proxy (justness) Mac Os Catalina
You should see the 'Congratulations!' messageshown below. If you don't, follow the instructionson the page to download and install Java.
Task 3: Start a Burp Transparent Proxy
At the upper right of the Mac desktop,click the magnifying glass icon,as shown below.In the search box, typeburpsuite. If Burp isalready on your Mac, it will be found,as shown below.
If you don't have Burp, open a Web browser,go to
and download the free version. Then repeatthe search.
In the search box, double-clickburpsuite_free.
If a box appears saying 'Are you sure...',as shown below, click Open.
TroubleshootingIf error messages appear, saying you cannotrun software from unknown sources, open'System Preferences', click'Security & Privacy', andconfigure your Mac to Allow apps downloadedfrom Anywhere,as shown below. |
If the Intercept button reads'Intercept is on', click it,so the message reads'Intercept is off',as shown below.
Click the Options sub-tab.At the top, in the 'Proxy Listeners'section, see if there are any entrieson the box shown to the right.
If there are, click each entry tohighlight it, and then clickRemove to remove them all,as shown below.
In Burp,Aat the top, in the 'Proxy Listeners'section, click the Add button.
On the Binding tab,enter a 'Bind to port' of 8080
Click the 'All interfaces'button,as shown below.
Click the 'Request handling'tab.
Click the 'Support invisible proxying'box,as shown below.
At the lower right of the box, clickOK. A box pops up,asking 'Are you sure...?'. ClickYes.
Burp should now show a Listeneron '*:8080' with the Invisible boxchecked,as shown below.
On the line showing '*:8080', clickthe Running check box twice tocheck it,as shown below.
Task 4: Forward Traffic to the Proxy with pf
Burp is now ready to gather trafficon port 8080 and forward it to theInternet.However, the mobile device doesn'tknow it should be sending traffic tothe proxy server, so Burp won'tever see it.It is possible to configure the mobiledevice to use a proxy, but not all appswill respect that setting. Some appswill just send traffic past the proxy,defeating our goal of auditing thenetwork traffic. A much better way toaudit apps is to use the Mac firewall'pf' to send all traffic from theBluetooth adapter through the proxy,so the mobile device won't know it'susing a proxy.
To use the 'pf' firewall, we needto create two files: 'pf.rules' and'pf.conf'. For our purposes thesefiles can be very simple.
In the Terminal window, execute thesecommands.
cdpwd
In my case, the directory was/Users/sambowne
Your directory will be different.
In the Terminal window, execute thiscommand:
nano pf.rulesThis rule redirects all TCP traffic fromthe Bluetooth connection to Burp,at 127.0.0.1:8080.
rdr pass on bridge0 inet proto tcp from any to any port 1:65535 -> 127.0.0.1 port 8080Press Ctrl+X, Y, Enter to savethe file.
In the Terminal window, execute thiscommand:
nano pf.confIn the second line, change/Users/sambowne to thecorrect directory you found above.
This configuration file tellspf where to find the rules file.
rdr-anchor 'forwarding'
load anchor 'forwarding' from '/Users/sambowne/pf.rules'Press Ctrl+X, Y, Enter to savethe file.
The next step is to test the files.
In the Terminal window, execute thiscommand:
sudo pfctl -vnf pf.confIf your files are correct,you'll see a 'Loading anchor forwarding...'message, followed by the line beginningwith 'rdr pass on bridge',as shown below.
If there are errors in your files,you'll see error messages here.If that happens, use nano to editthe files and correct the errors.
When your files pass this test withouterrors, execute this command tostart pf:
sudo pfctl -evf pf.confTask 5: Testing the Proxy
On your mobile device, in the Webbrowser, go toattack.samsclass.infoThe page should load,as shown below.
On your Mac, in Burp, click the'HTTP History' sub-tab.
You should see traffic tohttp://attack.samsclass.info,as shown below.
Burp is now intercepting and examiningyour mobile device's Internettraffic.There's no way for your mobiledevice to detect this man-in-the-middleattack for the HTTP protocol, which isone of the reasons it's an insecureprotocol.However, Burp won't be ableto get away with that with a properly-implementedHTTPS protocol.
On your mobile device, in the browser,go to samsclass.info --this is a secure page.
You should see a 'Cannot Verify Server Identity'message, as shown below.
Click Details.
A 'Certificate' box opens, showing thatthis certificate was 'Issued by PortSwigger CA',as shown below.
PortSwigger is the company that madeBurp, and Burp is creating fakecertificates for every website andsigning them. Thebrowser on your mobile device is correctlynotifying you that PortSwigger isnot a trusted CA, indicating thata possibleman-in-the-middle attack is in progress,